EternalBlue was developed by the NSA as a hacking tool to gather information in counterterrorism operations. For 5 years before the leak, it became one of the most useful exploits in the NSA’s cyber arsenal due to the massively popular operating system it exploits. However, it was stolen and leaked by the hacker group “Shadow Brokers”.
How it Works
EternalBlue exploits a vulnerability in Microsoft’s SMB protocol used for communication between devices. Denoted as CVE-2017-0144, the exploit works by taking advantage of vulnerabilities in the SMBv1 protocol specifically found in older versions of Microsoft operating systems, one of which is how it mishandles specially crafted packets from remote attackers that causes a buffer overflow and allows them to remotely execute code on the target computer.
Impact: Makes Everyone WannaCry
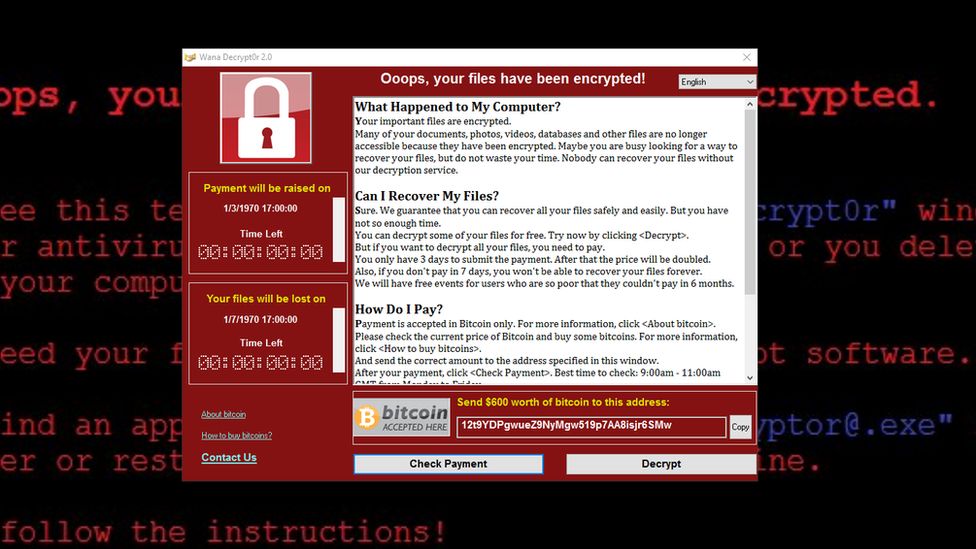
While EternalBlue by itself does not do anything aside from allowing remote code execution, it acts as a courier to deliver other malicious payloads to vulnerable machines. One major attack utilising EternalBlue is the WannaCry cyberattack which began on May 2017. WannaCry is a ransomware worm which had a spread rate of about 10,000 devices per hour, spreading across millions of vulnerable machines throughout the globe in a matter of days. This affected crucial infrastructures such as the NHS which had almost all their machines encrypted, causing chaos in healthcare systems throughout the UK.
The Patch
Microsoft immediately worked on a fix to patch this vulnerability after learning it has leaked to the public. A fix was released but required a software update to install the patch, which many machines did not immediately do. As a result, even to this day, millions of Windows systems remain unpatched and vulnerable to EternalBlue attacks.
